Table of Contents
- Chapter 6: AWS Networking Services - VPCs, Route53, and CloudFront
- Introduction to on-premises network
- Fundamentals of IP addressing and CIDRs
- IP address version 4 -IPv4
- Limitations of IPv4 addresses
- Businesses need internet access
- What about IPv6?
- Network sizes and classes
- What about subnet masks?
- What is subnetting?
- Classless Interdomain Routing (CIDR)
- Virtual Private Clouds (VPCs)
- All about subnets
- Internet access
- VPC security
- Network Address Translation (NAT)
- VPC peering
- VPC transit gateway
- Virtual Private Newtorks (VPNs)
- Direct Connect
- Learning about DNS and global routing with Amazon Route53
- Implemeting a robust CDN with Amazon CloudFront
- Introduction to Amazon API Gateway
Chapter 6: AWS Networking Services - VPCs, Route53, and CloudFront
Introduction to on-premises network
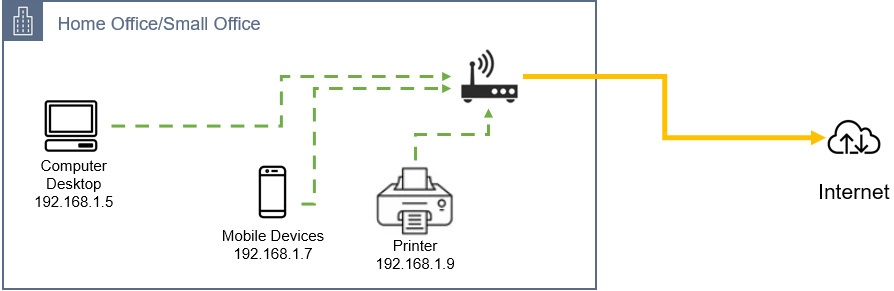
Every business will have some on-premises network. Even a home office have its own private network environment (computers, mobile phones and printers etc)
e.g. Home network
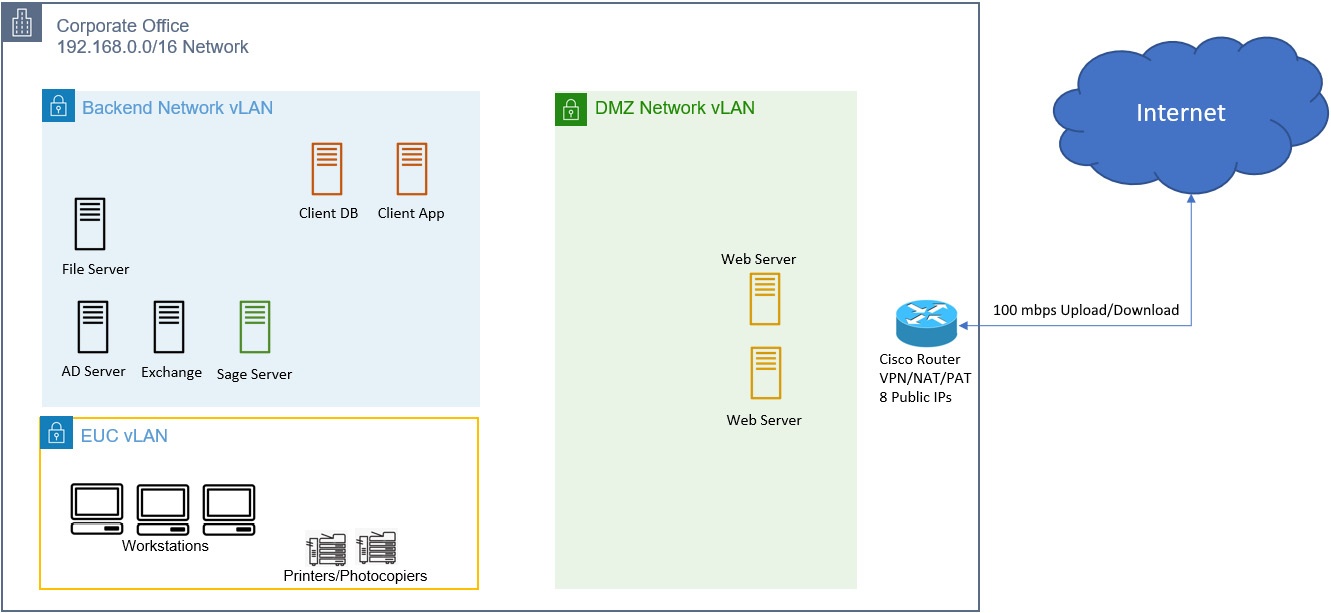
Basic corporate networks
Corporate network are more complex, as many corporate network need allow access from outside. e.g.
- If business need publish website from its network. Hence need firewall routers to allow only specific types of traffic to enter network from internet. And then direct them to appropriate server.
e.g. Basic office network
- DMZ stands for Demilitarized zone (DMZ), which is an area where services are deployed that can be exposed to internet
- In e.g. Corporate network is divided into 3 separate subnetworks. So, fine control can be applied to what type of traffic can enter each subnet
- DMZ vLAN can be configured to grant access over inbound HTTP/HTTPS traffic
- End User Computing (EUC) Virtual LAN (VLAN) is configured to not host such inbound connection, as no external access should visit this subnet. But traffic from EUC are permitted, so employee can access internet
AWS virtual network also need to be configured to suit corporate need
Fundamentals of IP addressing and CIDRs
Note: Refer to textbook for details. As this is about network foundamentals
IP address version 4 -IPv4
Refer to textbook for details.
Limitations of IPv4 addresses
- IPv4 address has 32 bits in length. Hence, max number of addresses is 4,294,967,294
- 4 billion address is not enough for modern society.
- Internet Assigned Numbers Authority (IANA) define following IP address for private us only:
10.0.0.0/8IP addresses:10.0.0.0 - 10.255.255.255.255172.16.0.0/12IP addresses:172.16.0.0 - 172.31.255.255192.168.0.0/16IP addresses:192.168.0.0 - 192.168.255.255
- Other addresses are public, hence routable on global internet
Businesses need internet access
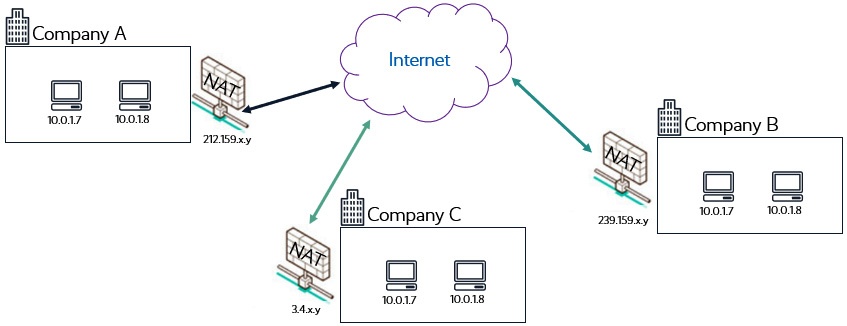
To facilitate internet connectivity, internal network can be configured to access internet via Network Address Translation (NAT) service (usually on router)
e.g. Business access internet via a NAT service configured on external router
- NAT service requries at least one single public IP address
- NAT service will route requests from internal devices to internet (vice versa), act as proxy between internet and internal network.
What about IPv6?
- IPv6 uses a 128-bit addresses (denoted in hex-adecimal format instead of decimal format)
- AWS offers IPv6 as option to setup cloud networks
Network sizes and classes
Refer to textbook for details
What about subnet masks?
Refer to textbook for details
What is subnetting?
Refer to textbook for details
Classless Interdomain Routing (CIDR)
Refer to textbook for details
Virtual Private Clouds (VPCs)
AWS provides a defualt VPC in each Region, when you created an account. They are designed to host EC2 instances, so they can access internet.
Custom VPCs can be configured to suit business requriements.
- When configuring a new VPC, you need to define an IP address block from one of private IP ranges (
10.x.x.x,172.x.x.x,192.x.x.x) - VPC span through entire region, hence workloads can be hosted in different AZs in same region
All about subnets
Depending on business requirement, multiple subnetworks can be configured in the custom VPC
- Subnet = subset of VPC
- e.g. if the IP address block of VPC is
10.0.0.0/16, publicSubnet-1can have CIDR block of10.0.1.0/24, andSubnet-2can have CIDR block10.0.2.0/24
- e.g. if the IP address block of VPC is
- Each subnet cannot overlap with each other.
- Subnets are restricted to a single AZ.
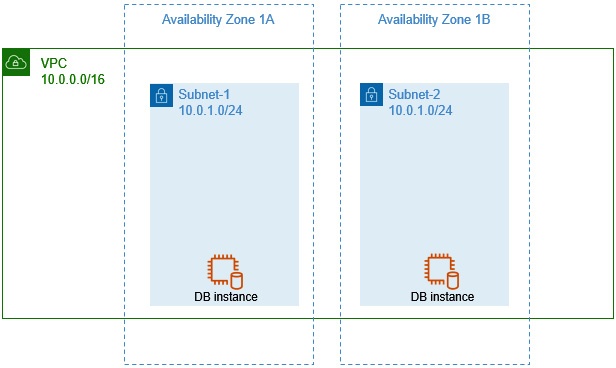
- e.g. application: create multiple mirrored subnets across multiple AZ, to provide redundancy for each other
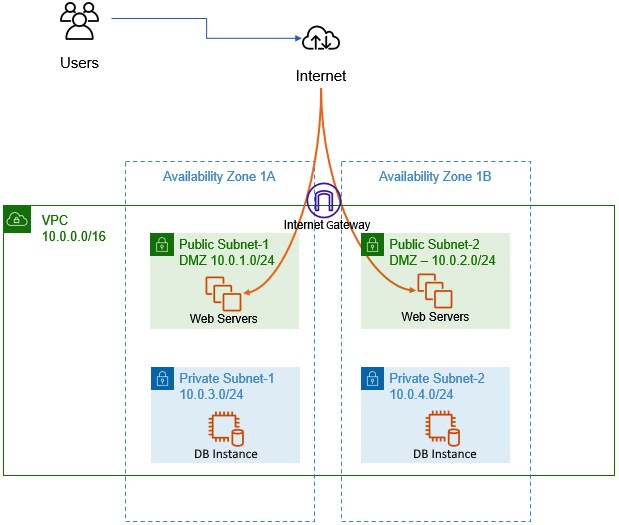
e.g. figure below show 2 DB instances across 2 subnets within 2 AZs of one VPC network
Internet access
- VPC need to be configured with internet access for its EC2 instances to visit internet.
- This can be done by deploy an internet gateway (shown in image below). It's a free component attached to VPC to grant VPC internet access
- If server need direct inbound access from internet (i.e. public customer can access the service), the server need to be deployed on public subnet, like shown in figure below. To make subnet public,
- subnet need be configured with route tables to have direct asccess to internet gateway
- EC2 instance or service need have public IP address, e.g. Elastic IP addresses provided by AWS
- a high-available VPC, that when AZ 1A have major outage, user can be redirected to web servers in public Subnet-2 of AZ 1B
Elastic IP address:
- Elastic IP addresses are static and remain in your account until you release them.
- can be assigned from one EC2 instance to another (i.e. respawn a new instance)
- it's free only whil they are associated with a running EC2 instance. If the EC2 instance stopped, hourly based fee will occur
VPC security
VPC firewall security ensure proper management of resource access.
e.g. only web server in the public subnet can make updates to backend database. And public visit should not have direct access to the backend DB
AWS offers 2 types of security service to the need:
- Security group = a firewall that's designed to allow dev to configure what type of traffic are permitted (inbound and outbound) to EC2 instance.
- When an EC2 instance launched, a security group need to be assigned, which contains rules for inbound/outbound traffic.
- Up to 5 security groups can be assigned on a single instance.
- Each VPC has a default security group.
- Default security group:
- allow all traffic inbound, but the source of traffic is from the security group itself. e.g. 2 EC2 within the default VPC can talk to each other.
- Not allow any traffic to inbound from other sources, until rules are created. i.e. prevent unsolicited traffic reaching the EC2
- e.g. Configure an appropriate inbound rule for HTTP and specify source of traffic, if need a server on standard HTTP protocol.
- Stateful: Response traffic to outbound request (i.e. sent from EC2) are permitted. (i.e. security group is aware of the state of traffic)
- Default security group:
- Features:
- Can configure allow rules, but cannot configue deny rules.
- Can specify separate rules for inbound and outbound traffic
- Can filter traffic based on protocols and port numbers.
- Source/destination of one security group can be another security group, hence constructing layered security policies.
- Network Access Control Lists (NACLs) = firewall service designed to protect entire subnet
- Instead of protecting each single EC2 instance, it allow/deny traffic from/to subnet
- Each VPC has a default NACL, which allow ALL inbound/outbound traffic
- NACLs are stateless. i.e. both inbound/outbound rules need to be configured.
Network Address Translation (NAT)
In corporate VPC, it's common practice to place critical resources in DMZ (private subnet).
- e.g. DB and backend server in DMZ can only be visited via frontend server or load balance, which are deployed in public subnet.
Problem: server in DMZ also need to visit internet, but it does not have public IP.
Solution: configure NAT service to allow DMZ resources to access internet and allow inbound responses to them.
As shown in in Figure 6.2 (copied here)
- NAT service needs to be placed in public subnets of the VPC
- Need have one elastic IP address attached to it.
- configured route table, so allow internet-bound traffic from EC2 instaces in DMZ can access internet
- NAT service relay requests from EC2 instances in private subnet to internet
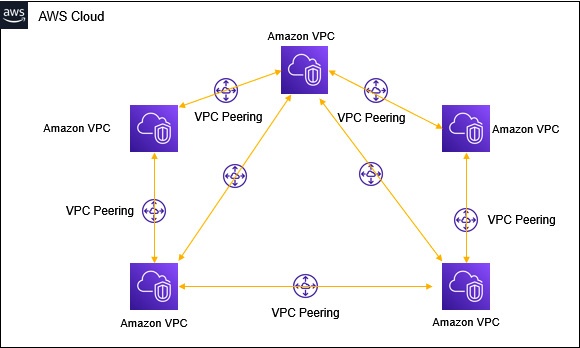
VPC peering
VPC peering connection = private network connections btw 2 VPCs.
- It's an AWS service allows to connect multiple VPCs into one VPC.
- Traffic between VPCs won't traverse public internet.
- Can connect VPCs in one AWS account, or btw multiple AWS accounts.
- Can connect between VPCs in same region, or across mulitple regions.
- Hence resources can be accessed/shared across different regions
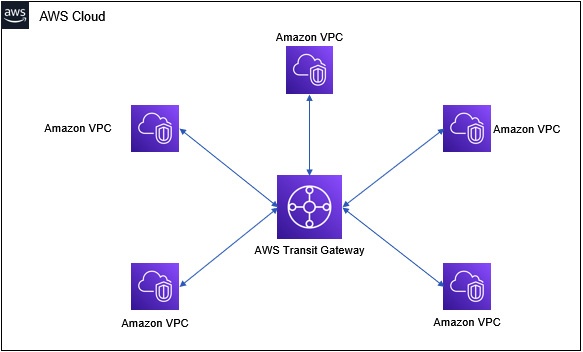
VPC transit gateway
- Problem of VPC peering: it's a one-to-one connection. Each peered VPCs need configured with route table to direct traffic. (as shown in figure above)
- AWS Transit Gateway can connect individual VPCs using hub-and-spoke model
Benefit of Transit Gateway
- Reduce architectural design overhead when connecting many VPCs
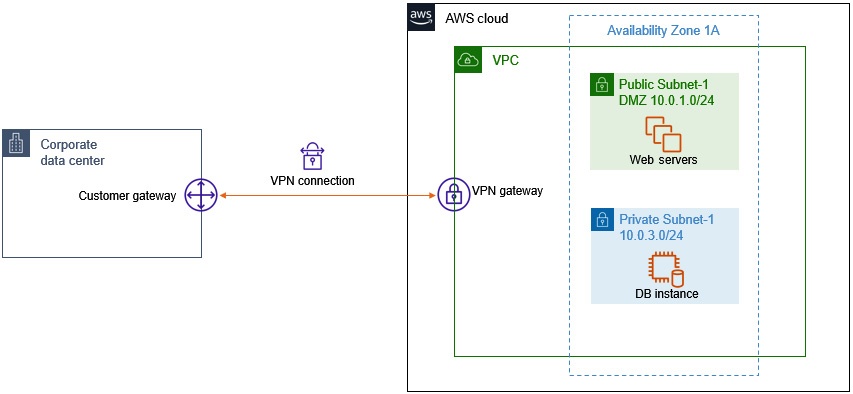
Virtual Private Newtorks (VPNs)
AWS VPC can be connected with corporate network, this type of connection is VPN
VPN = a secure encrypted site-to-site tunnel established btw 2 endpoints over public internet.
- offers AES128 or 256-bit Internet Protocol security (IPsec) encryption, so data can transfer securely between 2 endpoints.
How to set up VPN btw corporate network and VPC:
- Solution 1: Attach AWS Virtual Private Gateway (VPG) to VPC.
- Solution 2: Install customer gateway devices (e.g. Cisco) in on-premise network
Direct Connect
Learning about DNS and global routing with Amazon Route53
AWS Route53 = AWS's global DNS service to help translate human-readable names (URL) into IP address
Workflow of DNS:
- Browser visit website with name (e.g.
www.google.com), starting by sending a reqeust to local DNS service provider for IP address. - The authoritative DNS server responds with IP address, browser then establish a connection with the web
Process above is called Name Resolution
AWS Route53 offers 3 primary functions:
- Domain registration
- DNS routing
- Health Check
Domain Registration
This step is required before use the domain name for a website or web app. It can be done via domain register (e.g. Amazon Route53)
Steps of set name in domain register:
- choose a Top-Level Domain (TLD). e.g.
.com,.co.uk,.org, or.net - Purchase a lease duration for the domain name (from 1 year to 10 years)
- After registered a domain name, it need to be hosted with a DNS hosting service provider (which can be same company as the domain register)
When configuring domain names, we also need define a zone file, which will host resource records for domain name.
Hosted zones
Hosted zone = a container that's used to store and manage resource records and allows you to define how traffic is routed for your domain (e.g. example.com) and any sub-domains (e.g. portal.example.com)
2 types of hosted zones in Route53:
- Public hosted zone = a container that allows you to define how you want to route traffic for your domain name across public internet
- e.g. have a S3 resource
http://bucket-name.s3-website-Region.amazonaws.com, we can create an alias record that points the domain name to S3 endpoint.
- e.g. have a S3 resource
- Private hosted zone = container that allows you to define how you want to route traffic for your domain name across private networks, e.g. VPCs.
- e.g. use a friendly domain name
devserver.example.comto point to EC2 instance within VPCs
- e.g. use a friendly domain name
Details can refer to this Youtube: Route53 Private and Public Hosted Zone
DNS hostnames
Route53 Resolver is a DNS server for the VPC. It enable AWS to configure DNS hostnames for the instances you deploy in your VPC.
DNS hostnames consists of a hostname + a domain name. e.g. myserver.mycompany.com. It enable to create unique names for EC2 instances (or web services)
AWS provides 2 types of DNS hostnames:
- Private DNS hostnames: resolve to private IPv4 address of the instance.
- Public DNS hostnames: resolve a public NDS hostname to public IPv4 address of the instance outside the network of the instance.
Routing policies
Other than standard name resolution service, Rout53 offer complex routing policies and configurations.
- Simple routing policy: basic/default routing policy. Enable you to map a domain name to a single resource (e.g. IP address of web server or a DNS endpoint of an elastic load balancer).
- Policy engine won't check whether the resource is functioning and available.
- Failover routing policy: Two copies of resources across different Regions.
- 1 set of resource are defined as primary resource, the other as secondary resource.
- Route53 do health checks and determine whether primary resource is down and switch to secondary resource.
- Geolocation routing policy: Enable route traffic based on geographical location of users
- Useful when you want to direct traffic to resource in locations where distribution rights fits.
- Latency routing policy:
- Useful to route user traffic to Region that offers lowest latency
- Weighted routing policy: Route different ratios of total traffic to different resources associated with a single domain.
- e.g. Useful when performing gradual migration of total traffic from one resource to another.
Health checks
Route53 health check against resources, e.g. web servers, elastic load balances, or S3 static web.
3 types of health checks available
- Health check that monitor an endpoint
- Health checks that monitor other health checks
- Health check that monitor CloudWatch alarms
Traffic alarms and traffic policies
Implemeting a robust CDN with Amazon CloudFront
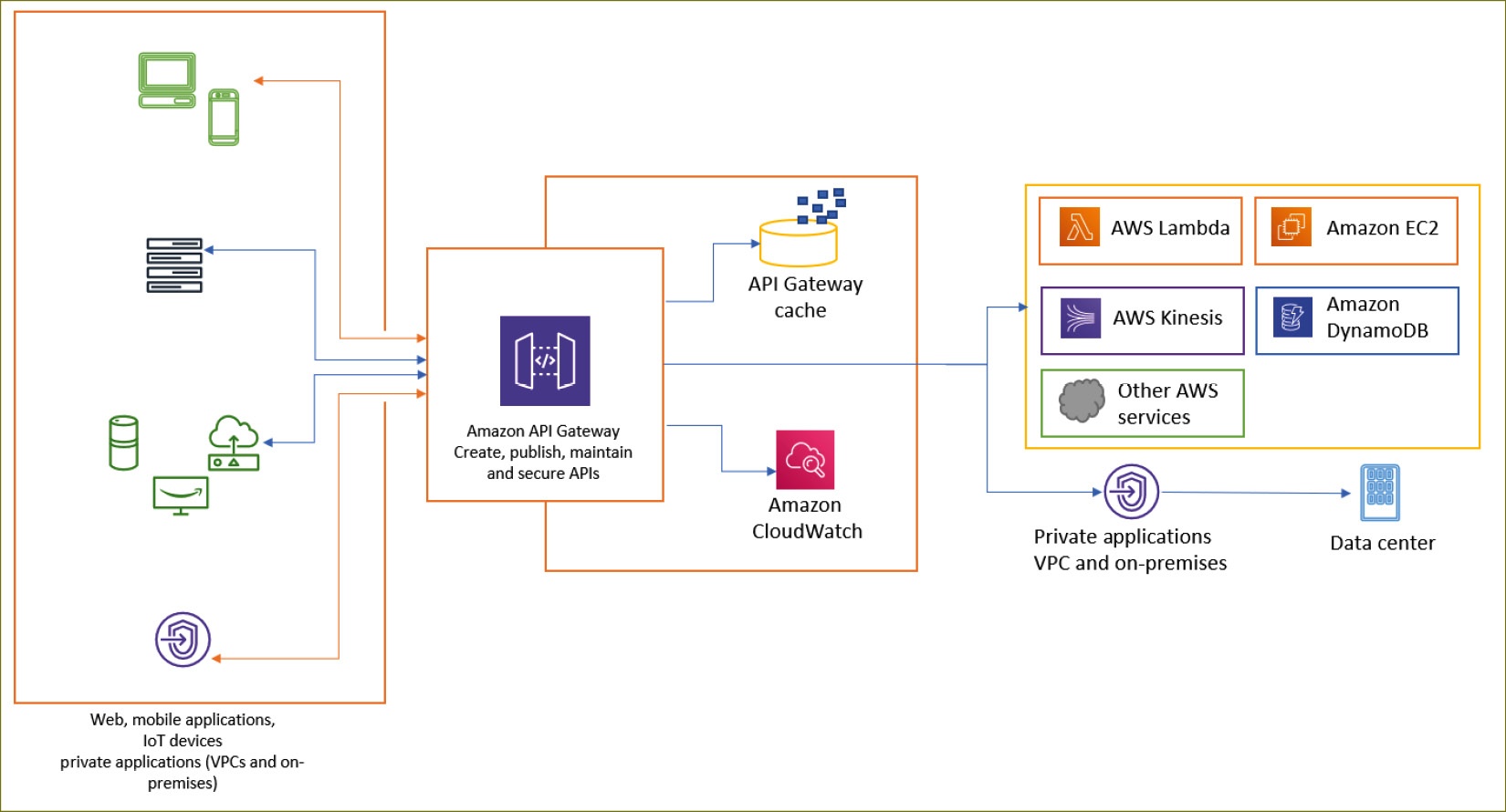
Introduction to Amazon API Gateway
API Gateway helps design app solution as microservice
- API Gateway act as an abstraction layer (i.e. a front door), to expose all API from all microservices.
- Request from different clients can be routed to various backend microservices.