Chapter 3: Exploring AWS Accounts, Multi-Account Strategy, and AWS Organizations
An AWS account provides ways of accessing public AWS services
Objective of this chap: how to have multiple AWS accounts and how to manage those accounts using service AWS Organisations.
Why have multi-account AWS environment?
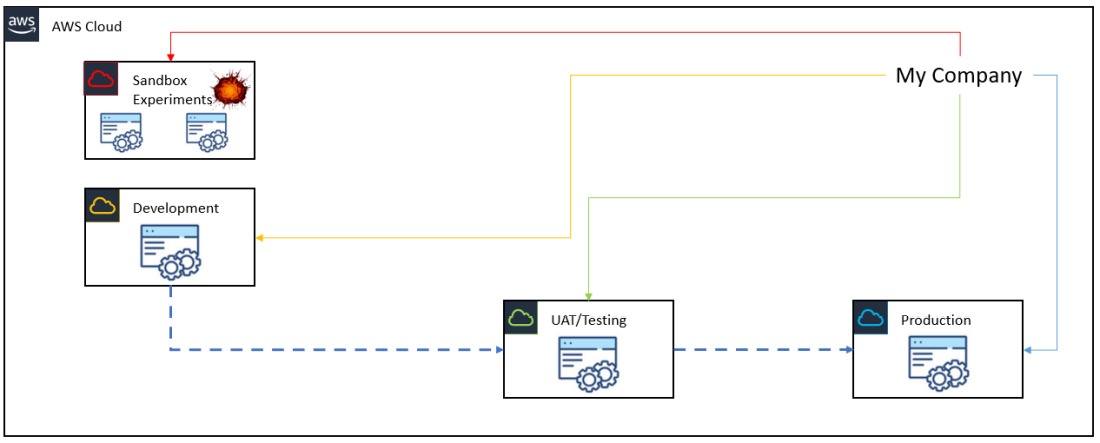
Separating workloads will help limit blast radius of catastrophic diasters (shown as below)
Benefits of having multi-account architecture:
- Administrative isolation between workloads: different business units have different levels of administrative controls (e.g. developer should not have full access to production account)
- Limited visibility and discoverability of workloads: an account provide natual boundary and enable developer to isolate workloads from any identity external to the account. (e.g. app deployed in one account cannot be accessed by user/app from another account)
- Isolation of security and identity management:
- Bad practise: In each AWS account, create multiple user identity accounts for the team. (e.g. developer user identity account, UAT tester account)
- Good practise: Host all users in a separate AWS identity management account. Then grant user access to other AWS accounts (e.g. dev env) using cross-account access
- Isolation of recovery or audit accounts: Duplicate workload placed in separate account for quick diaster recovery
AWS Landing Zone
AWS Landing Zone = an old service offered by AWS to help quick design/architect multi-account strategy
- offer customers a baseline blueprint to design/architect a multi-account env.
AWS Control Tower = new service to replace Landing Zone
AWS Control Tower
AWS Service used to automate the setup of new landing zone (called landing zone but not the same as AWS Landing Zone) using latest blueprint, e.g. deploy landing zone including:
- Creation of an AWS Org and multi-account setup
- Identity and access management with AWS SSO (Single Sign-On) default directory services
- Account federation using SSO
- Centralized logging using AWS CloudTrail and AWS Config
Landing zone deployed by AWS Control Tower have been configured with recommended security policies called guardrails, and customer can customerize their account
Managing multiple account - AWS Organizations
Introducing AWS Organisations
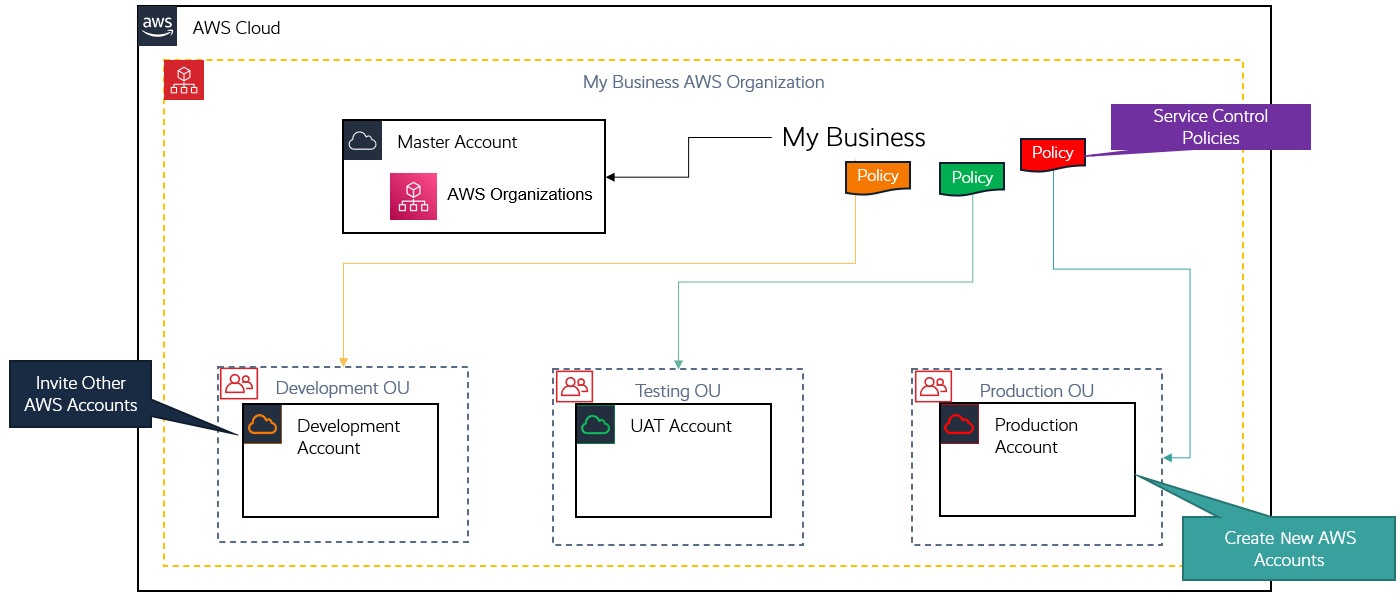
AWS Organization
- service enable company to centrally manage all AWS accounts
- It's free service
- Function:
- First, create one management account (i.e. master account)
- Then, invete or create additional AWS accounts that will become member accounts of the org.
Organizatio Unit (OUs)
- An OU = a logical group of one or more AWS accounts in the AWS Org. These accounts share similar functionality.
- OU is used to organize AWS accounts in hierarchies.
Service Control Policies (SCPs)
- applied to OUs, or directly to AWS Account (not good practice)
- Apply guardrails to services
Consolidated billing feature vs All features:
- AWS Orgs can be deployed using one of these 2 options
- Consolidated billing feature: Get basic management tools and ability to get a centralized bill for all your memeber accounts.
- All features: Get Consolidated billing, plus management capabilities for member accounts with Service Control Policies (SCPs)
Key benefit of Consolidated billing feature:
- Single bill
- Easy tracking
- Volume discounts
- Free services
How many AWS accounts do you need?
- Minimum number of account: isolate different dev env and production life cycles and offer redundancy and resilience against failure.
- Advice: create accounts to meet functional requirements and fullfill security controls.
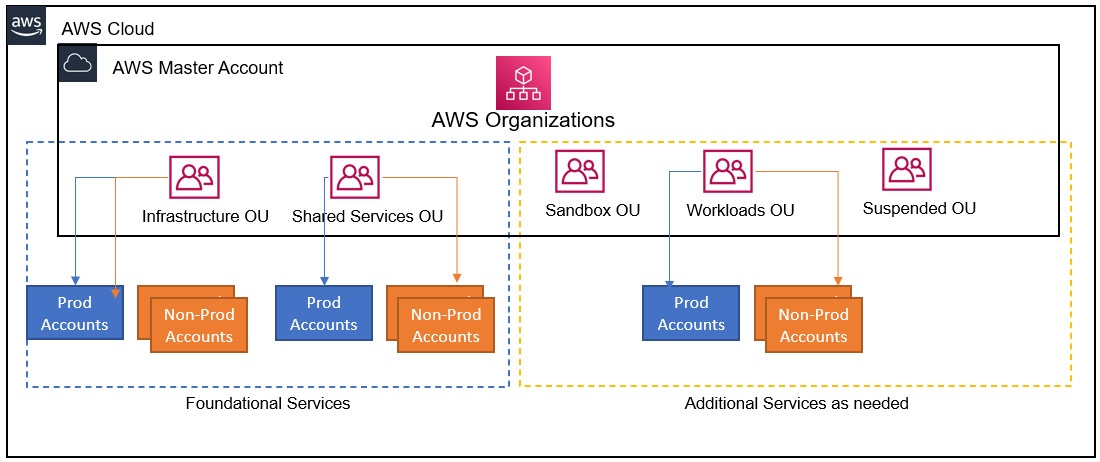
Core AWS OUs
Objective: Best practices for configuring AWS Orgs and OUs
Foundational core OUs: one infrastructure OU + security OU
- Infrastructure OU contains at least 1 Infrastructure services account
- The account contains all common servcies shared across accounts (e.g. directory service, network env, central repository for AMIs)
- Security OU contains at least 1 Security services:
- This account is a centralized IAM account to host individual user accounts, groups and roles.
Both fundational core OUs will contain non-production and production AWS Accounts.
Additional OUs
Other than AWS OUs, any number of additional OUs can be created depending on business use case.
AWS Free Tier accounts
Free Tier:
- Offered by AWS during first 12 months of opening any new account.
- Offer in Free Tier:
- 5GB of S3 storage up to 12 months, free of charge
- Launch a t2.micro EC2 instance for up to 750h/month
- Lightwight AWS RDS instance for up to 750h/month
Free tools
Other than 12-months Free Tier offering, some services are offered free forever. Most of them are used to deploy some resources, or manage other resources
e.g.
- AWS CloudFormation: service enable dev to define infrastructure (e.g. EC2, RDS etc) using code.
- Amazon Elastic Beanstalk: orchestration service that provisions necessary infrastructure components
Difference between CloudFormation and Elastic Beanstalk